What is DKIM? The Unsung Hero of Email Deliverability
Have you ever wondered how your email service provider knows whether an email is genuinely from who it claims to be? Or, how it known to put that annoying spam into your spam folder instead of your inbox? The answer is the often overlooked, but essential technology called DKIM (DomainKeys Identified Mail). Let's dive into what it is, how it works, and why it matters to everyone - not just the tech wizards.
What is DKIM?
DomainKeys Identified Mail (DKIM) is an email authentication method that helps prevent spoofing. It allows an organization to take responsibility for a message while in transit. DKIM works by attaching a digital signature, linked to the domain's name, to each outgoing email. This signature is verified against a public cryptographic key published in the domain's DNS records. If the signature matches, it confirms the email's integrity and its origin from the specified domain, enhancing trust and security in communication.
DKIM Signature Example:
When an email is sent from a server that uses DKIM, it attaches a special header to the message. This header includes a digital signature, created by encrypting the email's content using a private key known only to the sender's domain. This signature typically looks something like this in the letter header:
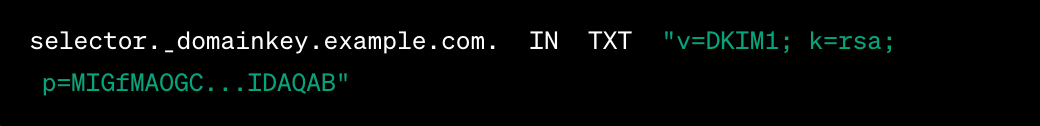
Public Key in DNS:
To verify this signature, the receiving email server looks up the sender's DNS records to find the public key. This key is published as a TXT record in the domain's DNS settings. It might look something like this:
In this record:
selectoris a domain-specific tag that identifies the DKIM public key.v=DKIM1specifies the DKIM version.k=rsadenotes the encryption algorithm used (RSA in this case).p=contains the actual public key.
Verification Process:
Upon receiving the email, the recipient's server uses this public key to decrypt the signature in the header. If the decrypted signature matches the content of the email, it confirms that the email has not been tampered with and indeed comes from the claimed domain, authenticating the sender's identity.
This process helps combat email spoofing and phishing by ensuring that the email is genuinely from the purported sender and that its content remains unaltered during transit.
How Does DKIM Work?
Imagine this: every time you send a letter, you put a unique wax seal on it. When the recipient gets the letter, they check the seal to verify it's genuinely from you. The same principle applies to DKIM.
When an email is sent, the sending server adds a unique DKIM signature to the email. This signature is based on the email content and a private key that only the sending server knows.
The recipient server, on receiving the email, sees this signature and goes to the sending domain’s DNS (Domain Name System) records. It retrieves a public key, which is like the other half of the unique seal. Using this public key, the recipient server can check if the DKIM signature is valid. If everything matches up, the email is confirmed as authentic and not tampered with during transit.
DKIM in Practice
Let’s imagine a scenario. You receive an email from your bank asking for your account details. Without DKIM, you’d have no way of knowing whether the email is genuinely from your bank or a scammer trying to steal your information.
But with DKIM, your email provider checks the DKIM signature of the email against the public key in your bank's DNS record. If it matches, the email is indeed from your bank. If it doesn't, it's likely a phishing scam and your email provider moves it to your spam folder, protecting you from potential fraud.
What Happens Without DKIM?
Without DKIM, it's like receiving letters with no way to confirm who really sent them. This could lead to phishing scams and spoofing, where spammers send emails pretending to be from legitimate sources. Additionally, your important emails might end up in your recipients’ spam folders, as their email providers can't verify their authenticity.
Why is DKIM Important?
DKIM plays a critical role in maintaining trust in communication. By verifying the sender and ensuring the email content hasn't been tampered with during transit, it prevents fraudulent emails from reaching your inbox. This protection is especially crucial for business letters, where phishing attacks can lead to substantial financial loss or damage to the company's reputation.
In addition to security, DKIM also improves email deliverability. When an email has a valid DKIM signature, it is more likely to pass through spam filters and reach the intended recipient's inbox.
Powerful Trio: DKIM, SPF, and DMARC
DKIM, along with SPF (Sender Policy Framework) and DMARC (Domain-based Message Authentication, Reporting & Conformance), forms a powerful trio that protects senders and recipients against email spoofing, phishing, and other attacks.
When your email has a valid DKIM signature, it's like it has a unique identification card. Internet Service Providers (ISPs) and email services see this and know that your email is legitimate, increasing the chances of it landing in the recipient's inbox instead of the spam folder.
But DKIM doesn't work alone in this process. SPF is another technology that works alongside DKIM. While DKIM verifies that an email hasn't been altered in transit, SPF verifies that the email has been sent from an approved server. The two together provide a double layer of security and trust, significantly enhancing email deliverability.
Meanwhile, DMARC brings it all together. It is a policy that uses both DKIM and SPF to decide what to do if an email fails these checks. When properly configured, DMARC can tell ISPs to reject or quarantine emails that fail SPF or DKIM checks, adding a further layer of protection.
When DKIM, SPF, and DMARC are used together, they create a robust shield that verifies your mails, protects your reputation, and improves your email deliverability.
Wrapping Up
In a world where digital communication is more important than ever, understanding technologies like DKIM is no longer just for the tech-savvy. These invisible superheroes work tirelessly to ensure our inboxes are safe and organized.
So, the next time you open your email, remember that a DKIM signature might have played a crucial role in ensuring that the message was safe to read and reached your inbox instead of landing in the spam folder.
To learn more about DKIM and other technologies that keep your communications secure, or if you're looking for help to optimize your business email deliverability, don't hesitate to reach out to us at info@alexshakhov.com. Our team of experts is always ready to assist you with any inquiries or support you might need. In the dynamic digital landscape, we're here to help you navigate with confidence.